Configure IAM functional ID
The "IAM service functional ID" is a user in the Domino directory. The IAM service operates with the rights of this user. This user is not a real person but rather what is referred to as a functional ID.
In this step we Register this user in the Domino directory. The user ID will be stored in the vault.
Create the IAM service user in the Domino directory
Using the HCL Domino Administrator perform the following actions to create the functional id user:
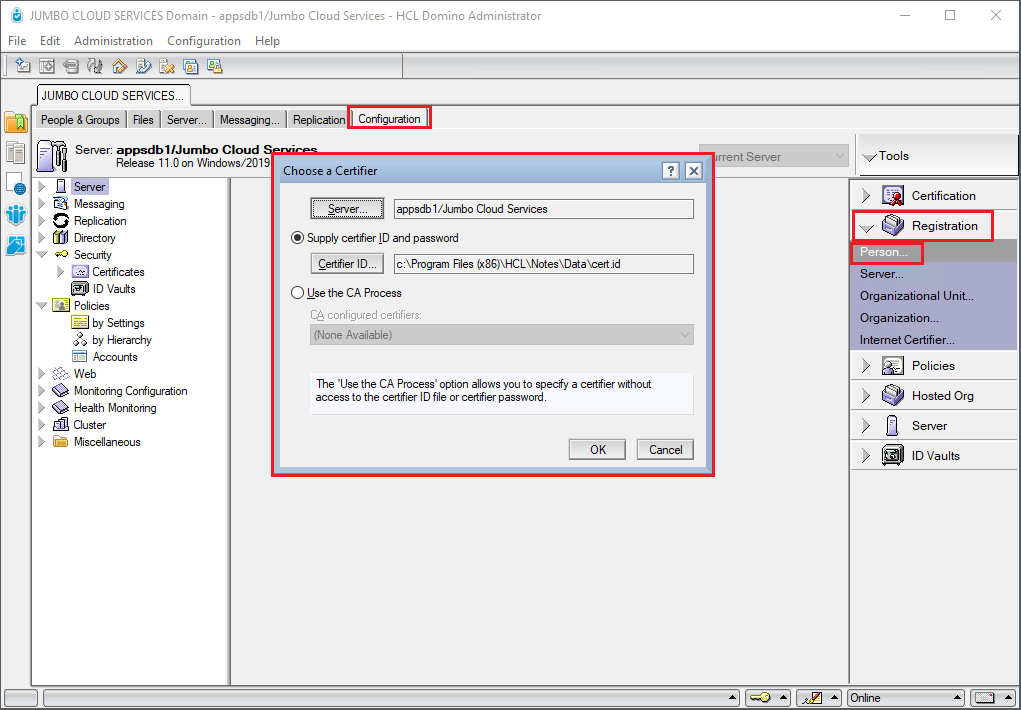
Select the Configuration Tab on the top Navigation Bar. Then, Open "Registration" on the right outline. Then, click "Person" to register a new functional id (Person) in the Domino directory.
You may be asked to locate the Certifier ID and to enter the password.
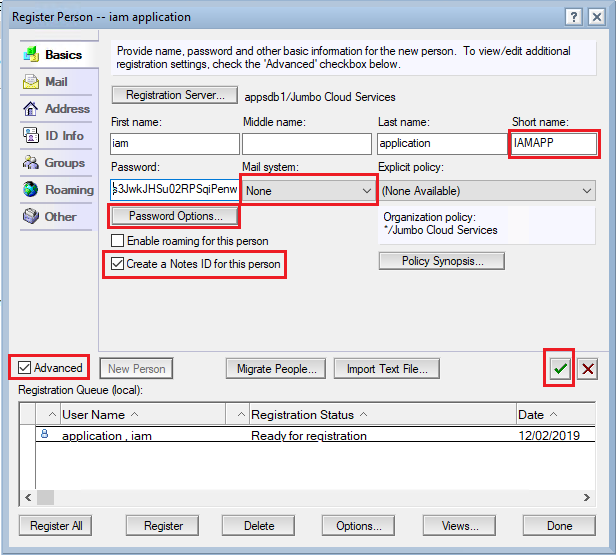
Complete the "Register Person" form, using the following guidelines:
- Enter a First Name and Last Name
- Enter a Short Name that is unique in the Domino directory. We will need to use the same short name to create the SSL certificate for the user.
- Enter a password in the "Password" field. This is the ID file password for the user. We enter this password in the IAM configuration when it requests "The cert's bounded functional ID's Notes password".
- Select "None" for Mail System.
- Be sure that the "Create a Notes ID for this person" check mark is enabled.
- Be sure that the "Advanced" check mark is enabled.
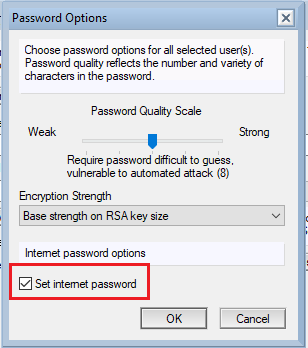
- Click the "Password Options" button. Select the "Set internet password" option. Then click OK.
Click the green check mark on the right side of the dialog. This stores all the settings and queues the user for registration. If you need to register multiple users at the same time you can queue more entries in the Registration Queue.
Click on the "ID Info" tab on the left of the dialog box. The dialog displays additional settings:
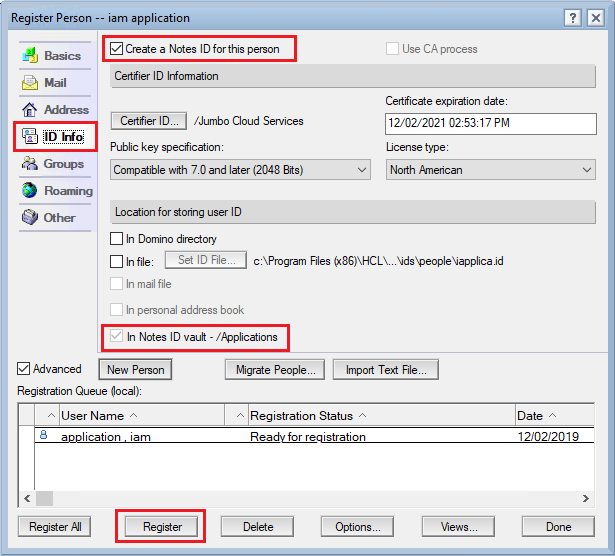
Be sure that the following check marks are enabled:
- "Create a Notes ID for this person"
- "In Notes ID vault" and that it shows the name of the vault that you created earlier.
If ok, then click on "Register" to create the user in the Domino directory.
Create the IAM service client certificate
Complete the following steps to create a client certificate issued by the Internal CA. The IAM service uses this client certificate to connect to Domino server. Proton running on the Domino server uses this client certificate to identify the identity of the user making the request. the Domino directory has the relationship between the IAM service user and the client certificate.
Create the private key
Use the following command to create a private key that is password
protected. It creates the file iamapp.key which is password protected
with the password: 1234. Change the password as needed.
c:\certs>openssl genrsa -passout pass:1234 -des3 -out iamapp.key 4096
Generating RSA private key, 4096 bit long modulus (2 primes)
.................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................++++
.............++++
e is 65537 (0x010001)
Create the CSR
Use the following command to create a certificate signing request (CSR). The
command creates the file iamapp.crt which contains the request to generate a
signed certificate with the subject name as indicated by the -subj "/O=Jumbo Cloud Servers/CN=iamapp" option.
The CN part of the subject is key to associating the user in the Domino
directory to the certificate. Earlier, we created the user with the short name
iamapp. The CSR must request the same short name from the CA.
c:\certs>openssl req -passin pass:1234 -new -key iamapp.key -out iamapp.csr -subj "/O=Jumbo Cloud Servers/CN=iamapp" -sha256
Sign the CSR
The Internal CA administrator performs the following steps to sign the CSR:
- create a temporary file containing certificate extensions to use in the signing operation.
- sign the CSR and generate the signed certificate.
Create the temporary file to specify extensions
Create a temporary file that specifies:
- the Extended Key Usage that specifies the key may be used for client authentication. (reference)
In our example, the temporary file contains the following data. The name of the file is not important, but be sure to use the same file name on the next step where this file is used.
c:\certs>type clientauth.txt
extendedKeyUsage=clientAuth
Sign the CSR with extensions
Issue the following command to sign the CSR. The command provides two key pieces of data:
- The name of the temporary file containing the signing extensions:
-extfile clientauth.txt - Certificate expiration:
-days 500
c:\certs>openssl x509 -passin pass:1234 -req -days 500 -in iamapp.csr -CA internalca.crt -CAkey internalca.key -out iamapp.crt -CAcreateserial -CAserial ca.seq -extfile clientauth.txt
Signature ok
subject=O = Jumbo Cloud Servers, CN = iamapp
Getting CA Private Key
This operation creates the file iamapp.crt which contains the signed
certificate.
Inspect the certificate
Issue the following command to inspect the certificate file
appsdb1.csr. Note that the output includes the following:
- The subject name for the certificate. The is the name requested in the CSR.
- The Internal CA as the signer of the certificate.
- The extension attributes for key usage.
- The certificate validity dates
c:\certs>openssl x509 -in iamapp.crt -text -noout -certopt no_pubkey,no_sigdump
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
36:2d:f4:60:89:33:35:cc:27:1d:32:b8:cf:27:8c:b8:31:50:58:64
Signature Algorithm: sha256WithRSAEncryption
Issuer: O = Jumbo Cloud Services, CN = Internal Certificate Authority
Validity
Not Before: Dec 2 20:52:42 2019 GMT
Not After : Apr 15 20:52:42 2021 GMT
Subject: O = Jumbo Cloud Servers, CN = iamapp
X509v3 extensions:
X509v3 Extended Key Usage:
TLS Web Client Authentication
Associate the IAM service user with the IAM client certificate
Use the following Domino server console command to load the client certificate into the person document in the Domino directory.
This command uses the Common Name (CN) part of the name in the certificate to find the person document. If found, it will import the certificate into the person document.
When Proton authenticates a network request the request must provide a valid certificate, that is trusted according to the keyring file. The certificate must have a subject name that matches a user in the Domino directory. The user's person document must have the same certificate the client provided in the request.
> load proton --importcert c:\certs\iamapp.crt
[07A8:0002-16D0] 12/02/2019 03:58:24.54 PM PROTON_CMD> import_certificate: c:\certs\iamapp.crt
[07A8:0002-16D0] 12/02/2019 03:58:24.55 PM PROTON_CMD> Certificate::init: enter
[07A8:0002-16D0] 12/02/2019 03:58:24.57 PM PROTON_CMD> Certificate::init: subject: CN=iamapp/O=Jumbo Cloud Servers
[07A8:0002-16D0] 12/02/2019 03:58:24.57 PM PROTON_CMD> Certificate::init: exit
[07A8:0002-16D0] 12/02/2019 03:58:24.58 PM PROTON_CMD> Updating note 0x1FEE for 'iamapp'
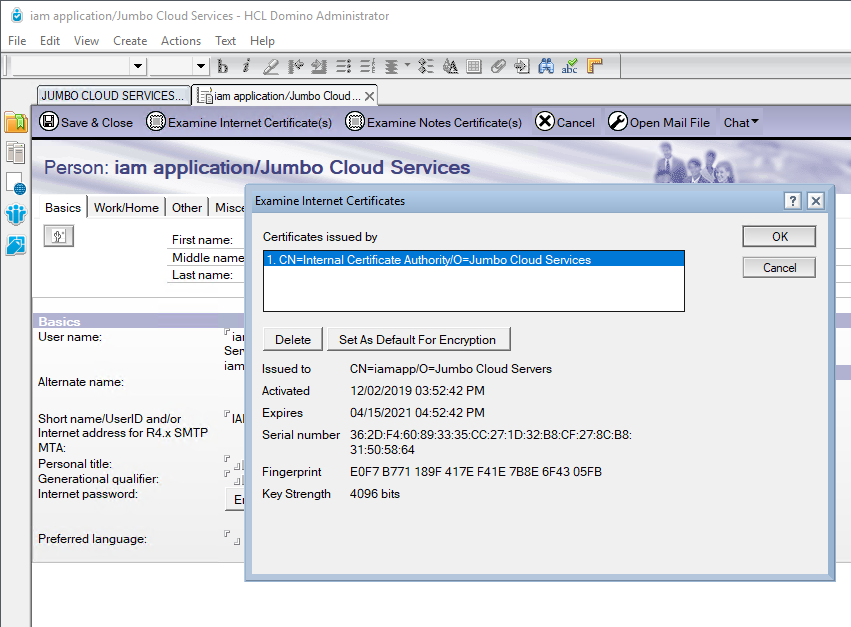
Inspect the IAM client certificate in the Domino directory
To inspect the client certificate associated with a user in the Domino directory perform the following:
- Locate the Person document for the IAM service user in the Domino directory.
- Click on "Edit Person" button to open the document for editing.
- Click on "Examine Internet Certificate(s)" button to open the dialog box as shown below.
- Select one of the entries in the "Certificates issued by" list in the dialog to view the details of the certificate.