LDAP Configuration
IAM does user authentication through integration with an identity provider (IdP). Currently, IAM supports two kinds of IdPs:
- Domino LDAP: IAM supports using Domino through LDAP as IDP, which means you can configure IAM to use user information in the Domino directory when authenticating users.
- Microsoft Active Directory: IAM supports using Active Directory through LDAP as the IdP, you can choose this configuration when your Domino Directory is integrated with Active Directory.
IDP Configuration
To configure the IDP, click Configuration in the left panel or click the
Configure LDAP button in the Dashboard.
| Field | Description | Example |
|---|---|---|
| URL | The URL of the LDAP server, including the full qualified DNS name and the port. You can omit the port if the LDAP server uses a default port(389 for LDAP, 636 for LDAPS) | ldaps://domino.server:636 |
| Base DN | The base DN from which to search for the provided user credentials | o=myorg |
| Search Fields | The field to search for the provided user credentials | |
| Bind DN | The DN to bind to for for ldapsearch operations | cn=ldapAdmin,dc=company,dc=com |
| Password | The password for the LDAP Bind DN | |
| Test user | Used for LDAP verification. Input an existing user in the LDAP directory | testuser@myorg.com |
| Notes DN Attribute | Optional. Only used when using Active Directory as IDP, and Directory assistance is configured on Domino to look up user information in Active Directory. | description |
1. Domino LDAP
1.1 URL
The protocol part should be LDAP or LDAPS (LDAP over SSL), you can check
whether SSL is enabled for your LDAP to choose the correct protocol prefix:
- From the Domino Administrator, click the Configuration tab.
- On the left pane, double click the server document to open it.
- Click Ports... tab -> Internet Ports... tab -> Directory tab
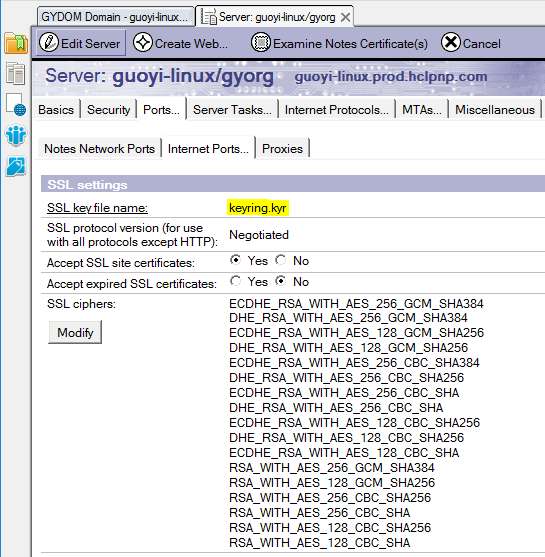
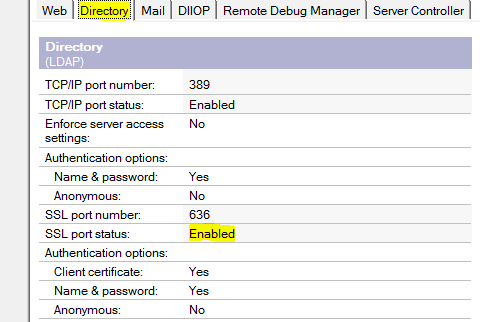
The host name part should be your Domino’s fully qualified internet host name. You can omit the port number if your LDAP or LDAPS service uses the default port number. The default port number for LDAP is 389, and for LDAPS is 636.
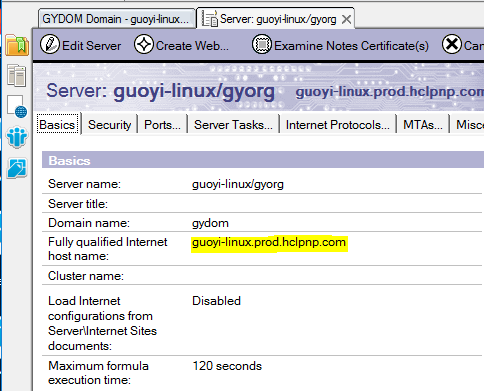
Example
1.2 Base DN
This field should contain the base DN from which to search for the provided user credentials. Use Domino Administrator to determine the Base DN:
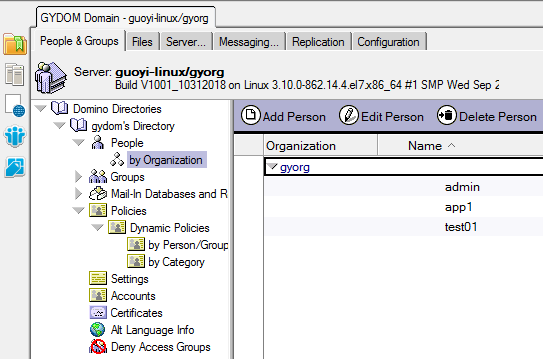
- From the Domino Administrator, click the People & Groups tab.
- On the left pane, click Domino Directories and find the Domino server which is your IAM's LDAP server. Click the server’s Directory -> People -> by Organization.
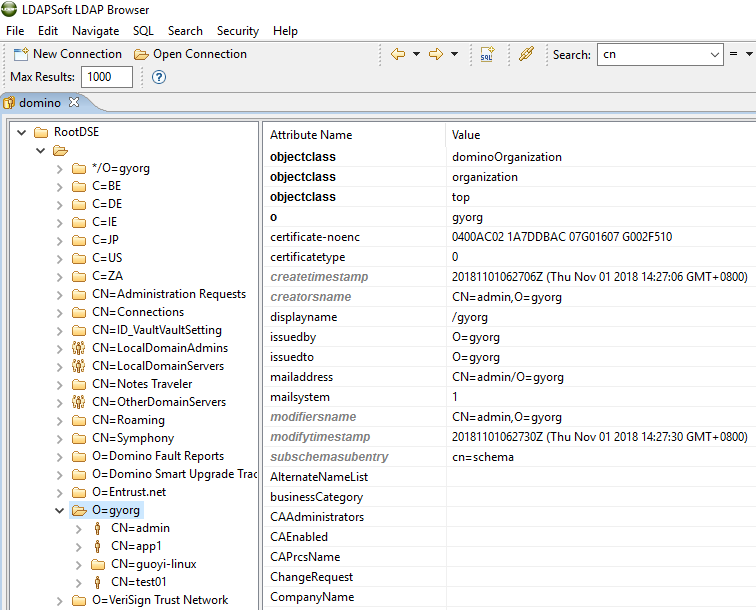
- In the right view, select the organization. Use the canonical name for the organization as the Base DN. For example if the organization is gyorg, specify O=gyorg as the Base DN.
Alternatively, determine the base DN by using a third-party software such as LDAP browser.
1.3 Search Fields
Specify the directory attribute to use to search for users in the directory. To search for multiple attributes, separate them by commas.
Use the Domino Administrator to see the available attributes:
- From the Domino Administrator, click the Configuration tab.
- On the left pane, click Directory -> LDAP -> Domino LDAP Schema -> LDAP – Attribute Types to see the available attributes.
- Specify one or more attributes in the LDAP name column in the Search Fields settings, for example, mail, cn, uid, displayName.
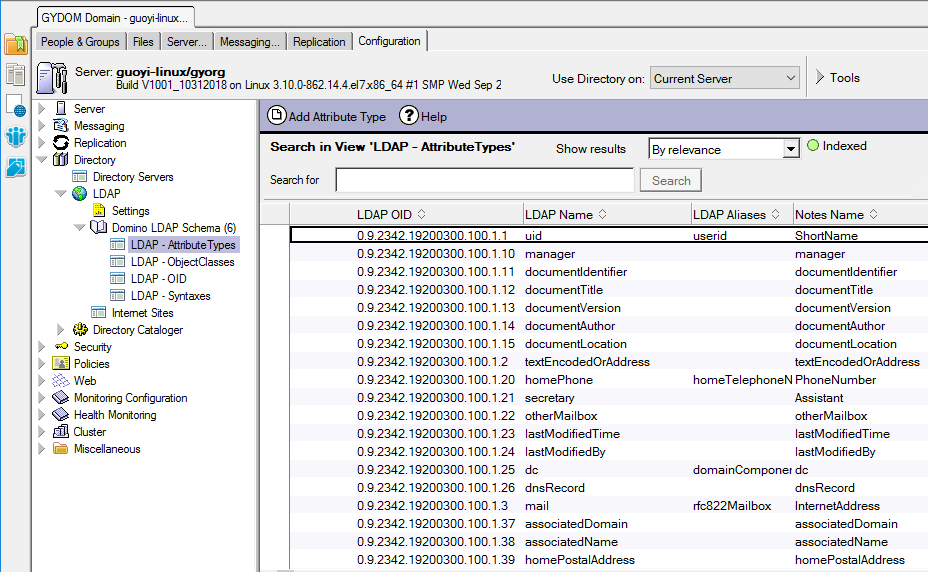
Since all Domino document fields are seen in this view, it's not convenient to find the attribute what you want from the huge list, it’s a good idea to use third-party software such as LDAP browser to see a complete list of attributes.
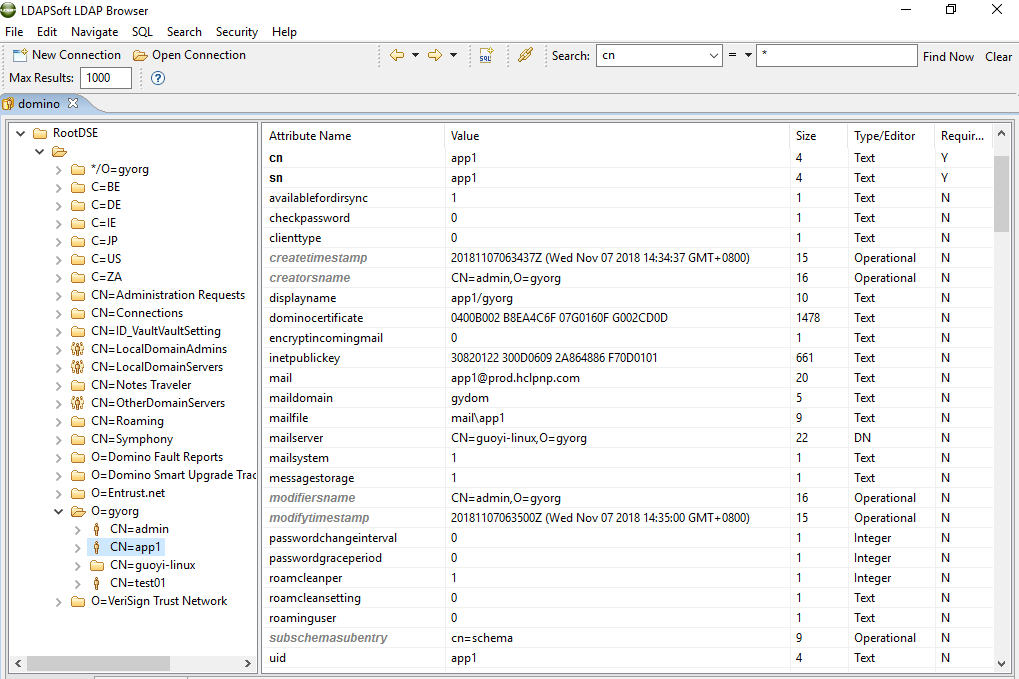
1.4 Bind DN
The DN to bind for ldapsearch operations.
You can use any user with an internet password to bind the Domino LDAP. Any of the following name format are acceptable for authentication:
- a. Short name, e.g. admin
- b. Notes format distinguished name, e.g. cn=admin/o=gyorg
- c. LDAP format distinguished name, e.g. cn=admin,o=gyorg
- d. Hierarchical name, e.g. admin/gyorg
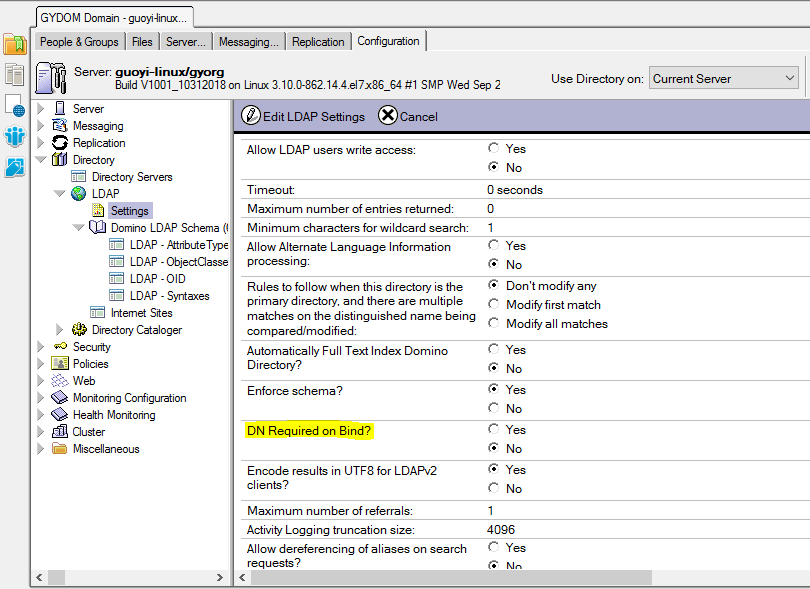
If you select Yes on ‘DN Required on Bind’ option in LDAP settings view, you should use the LDAP format distinguished name (item c. above) to bind.
1.5 Password
The internet password for the LDAP Bind DN.
1.6 Test User
Test User is used for LDAP verification. Input an existing user in LDAP directory, and click the 'Verify' button to check whether the user exists in this LDAP directory.
1.6.1 Example 1
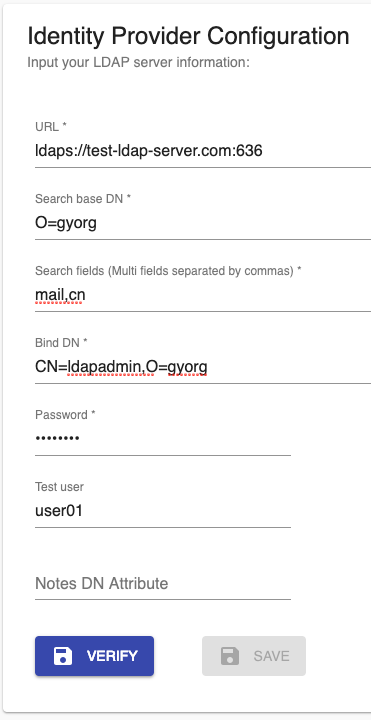
These settings perform the following Domino ldapsearch command. You will get a success notification when finding the first entry.
ldapsearch -h test-ldap-server.com -p 636 -b "O=gyorg" \
-D "CN=ldapadmin,O=gyorg" -w "passw0rd" "(|(mail=user01)(cn=user01))"
1.6.2 Example 2
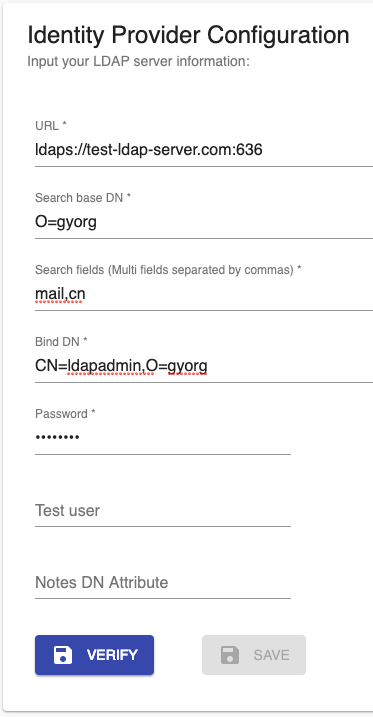
These settings perform the following Domino ldapsearch command. You will get a success notification when finding the first entry.
ldapsearch -h test-ldap-server.com -p 636 -b "O=gyorg" \
-D "CN=ldapadmin,O=gyorg" -w "passw0rd" "(|(mail=*)(cn=*))"
1.7 Notes DN Attribute
Omit this field if using Domino LDAP server. This field is only used when using Active Directory as IDP, and Directory assistance is configured on Domino to look up user information in Active Directory.
1.8 LDAPS
If LDAPS is enabled for Domino, make sure server certificate for LDAPS connections are signed by a well-known CA, or you will need to put the CA certificates into IAM's trust store.
Domino stores certificates in a key ring file. You can find the key ring
file name in Server Document (Ports... -> Internet Ports.. ->
Directory -> SSL Settings).
Then you can use kyrtool tool to check the certificates used by LDAPS
connections:
Note: Before Domino 11, the bin directory was in /opt/ibm/domino/
/opt/hcl/domino/bin/tools/startup kyrtool show certs -k <SSL keyfile>
Example:
/opt/hcl/domino/bin/tools/startup kyrtool show certs -k keyring.kyr
This command displays all the certificates in Domino keyring. Find the content of the root CA certificate from the output and copy it into a PEM file. Then copy the PEM file into IAM's trust store. (config/certs/ca).
Note: you only need to copy the content between
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----.
An example PEM file constructed from kyrtool output:
-----BEGIN CERTIFICATE-----
[content of root CA certificate]
-----END CERTIFICATE-----
...
Refer to Installing and Running the Domino keyring tool for the usage of kyrtool.
2. Microsoft Active Directory(AD)
2.1 URL
The host should be the DNS name, which you can see in Active Directory Users and Computers:
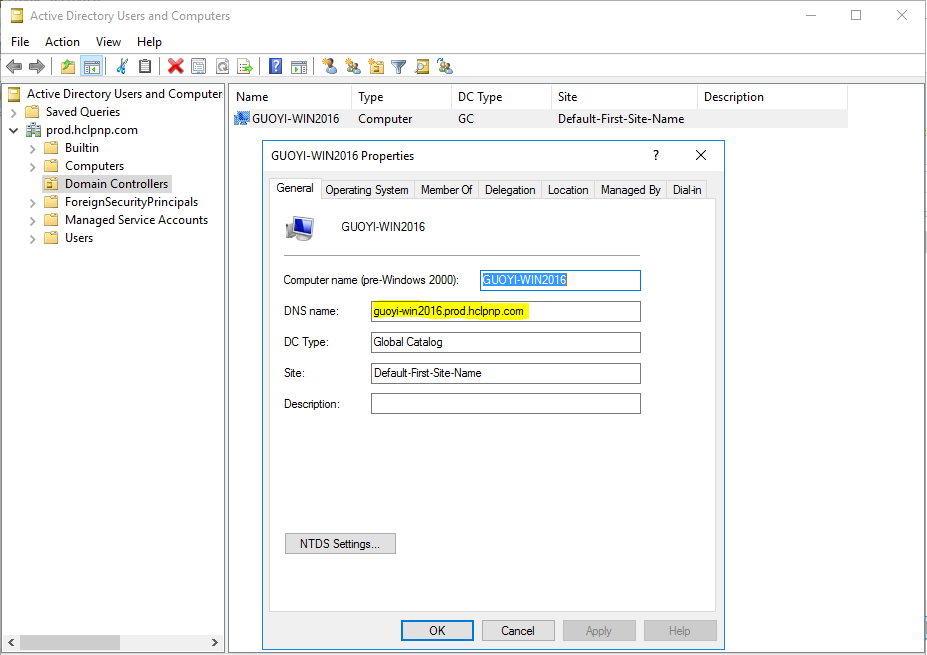
2.2 Base DN
You can check base DN using LDAP Browser.
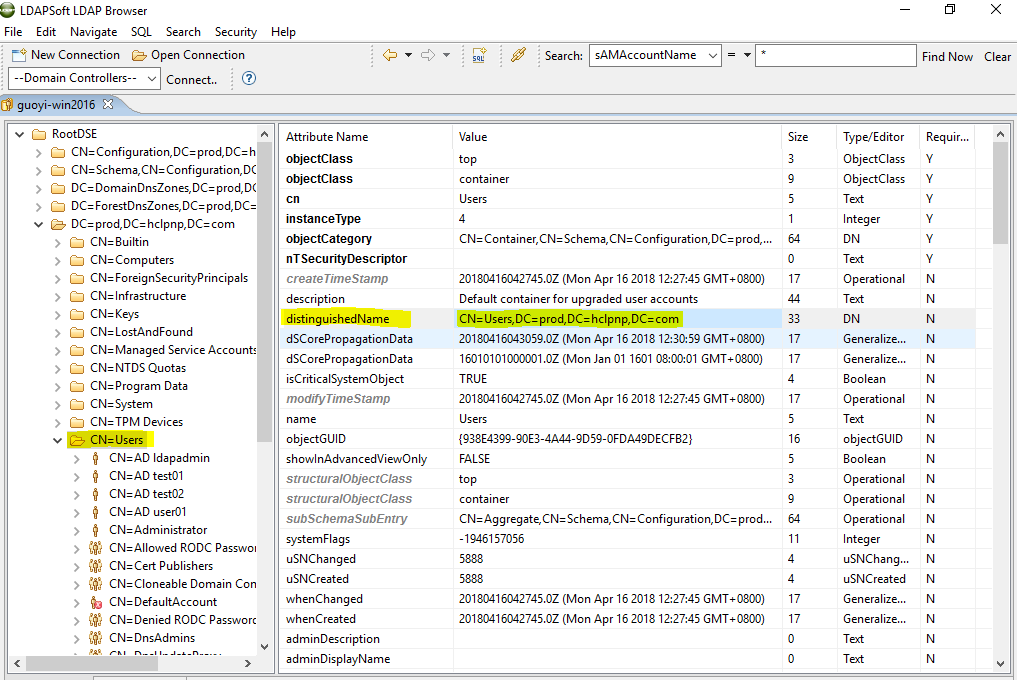
2.3 Search Fields
You can check search field using LDAP Browser.
2.4 Bind DN
You can use any user to bind AD LDAP, and you can use any one of the following name formats for authentication:
- a. User logon name, e.g. AD User01
- b. Pre-Windows 2000 user logon name, e.g. prod\user01
- c. Distinguished name, e.g. CN=AD User01,CN=Users,DC=prod,DC=hclpnp,DC=com
- d. User principal name, e.g. user01@prod.hclpnp.com
2.5 Password
The password for the LDAP Bind DN
2.6 Test User
The same with Domino LDAP guide.
2.7 Notes DN Attribute
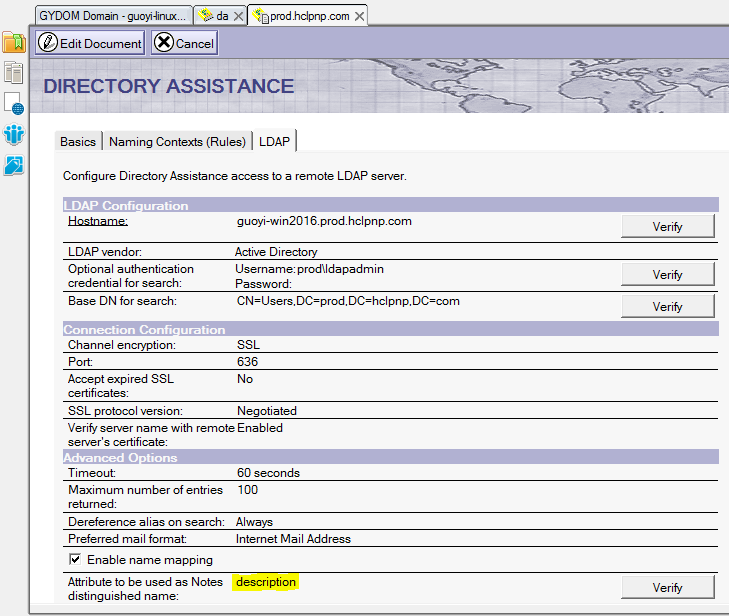
If using Active Directory as IDP, and Directory assistance is configured on Domino to look up user information in Active Directory, then we recommend you fill the Notes DN Attribute field for performance purpose. Use the Domino Administrator to see the Notes DN Attribute:
- From the Domino Administrator, click the Configuration tab.
- On the left pane, click Directory -> Directory Assistance.
- Open the directory assistance document in the right view.
- Click the LDAP tab, and find the 'Attribute to be used as Notes distinguished name' field.
2.8 LDAPS
If LDAPS is enabled for Active Directory, contact your AD Admin to check whether the certificate for LDAPS connections is signed by a well-known CA. If not, copy the root CA certificate into one PEM file and copy it to IAM trust store (config/certs/ca).
An example PEM file:
-----BEGIN CERTIFICATE-----
[content of root CA certificate]
-----END CERTIFICATE-----
...
References
For Domino LDAP service, refer to The Domino LDAP Directory