Configure the user ID for connecting to Proton
The ptest tool runs with the rights of a user in the Domino directory. Follow these steps to
prepare an existing user and to run the ptest tool with the access rights of the user.
Identify the Domino user
We will configure the demonstration utility, ptest, to execute with the
rights of an existing user. The first step is to identify the Domino user that
will run ptest. Find the person document in the Domino directory and make a
note of the user's short name.
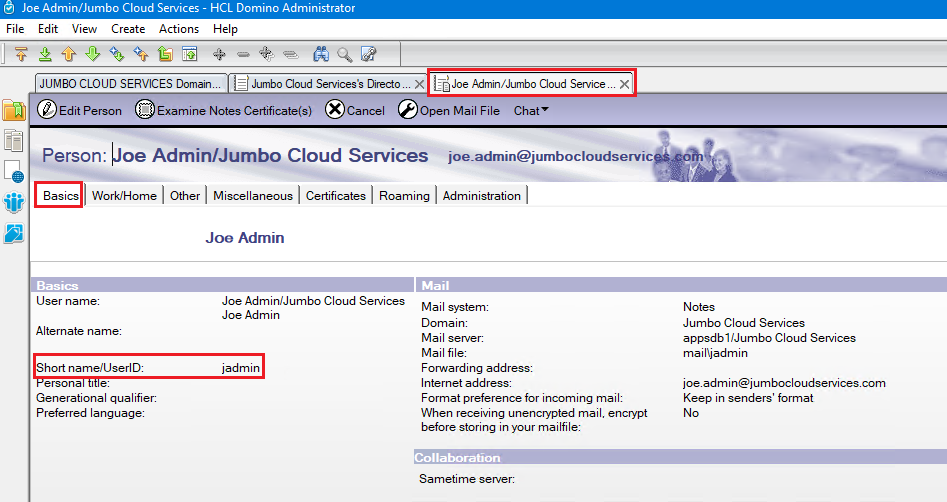
In our example, the Domino user's short name is: jadmin.
Create the client certificate
The steps to create the client certificate are:
- Create the private key.
- Create the certificate signing request (CSR).
- Sign the CSR.
Create the private key
Use the following command to create a private key that is password protected. It creates the file jadmin.key which is
password protected with the password: 1234. Change the password as needed.
c:\certs>openssl genrsa -passout pass:1234 -des3 -out jadmin.key 4096
Generating RSA private key, 4096 bit long modulus (2 primes)
..++++
...................................................++++
e is 65537 (0x010001)
The ptest tool uses an unprotected form of the private key. Use the following command to create the
file admin-open.key which is the same key as jadmin.key but the file is not protected with a password.
c:\certs>openssl rsa -passin pass:1234 -in jadmin.key -out admin-open.key
writing RSA key
Create the CSR
Use the following command to create a certificate signing request (CSR). The command creates the file jadmin.crt
which contains the request to generate a signed certificate with the subject name as indicated by the
-subj "/O=Jumbo Cloud Servers/CN=jadmin" option.
The CN part associates the user in the Domino directory to the certificate.
Earlier, we determined that the administration user has the short name jadmin.
The CSR must request the same short name from the CA.
c:\certs>openssl req -passin pass:1234 -new -key jadmin.key -out jadmin.csr -subj "/O=Jumbo Cloud Servers/CN=jadmin" -sha256
Sign the CSR
The Internal CA administrator performs the following steps to sign the CSR:
- Create a temporary file containing certificate extensions to use in the signing operation.
- Sign the CSR and generate the signed certificate.
Create the temporary file to specify extensions
Create a temporary file and add it to the Extended Key Usage attribute. This attribute indicates that the key may be used for client authentication. The name of the file is not important, but be sure to use the same file name when you sign the CSR in the next step.
c:\certs>type clientauth.txt
extendedKeyUsage=clientAuth
Sign the CSR with extensions
Issue the following command to sign the CSR. The command provides two key pieces of data:
- The name of the temporary file containing the signing extensions: -extfile clientauth.txt
- Certificate expiration: -days 500
c:\certs>openssl x509 -passin pass:1234 -req -days 500 -in jadmin.csr -CA internalca.crt -CAkey internalca.key -out jadmin.crt -CAcreateserial -CAserial ca.seq -extfile clientauth.txt
Signature ok
subject=O = Jumbo Cloud Servers, CN = jadmin
Getting CA Private Key
This operation creates the file jadmin.crt which contains the signed certificate.
Inspect the certificate
Issue the following command to inspect the certificate file jadmin.crt. Note that the output includes the following:
- The subject name for the certificate. The is the name requested in the CSR.
- The Internal CA as the signer of the certificate.
- The extension attributes for key usage.
- The certificate validity dates
c:\certs>openssl x509 -in jadmin.crt -text -noout -certopt no_pubkey,no_sigdump
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
36:2d:f4:60:89:33:35:cc:27:1d:32:b8:cf:27:8c:b8:31:50:58:66
Signature Algorithm: sha256WithRSAEncryption
Issuer: O = Jumbo Cloud Services, CN = Internal Certificate Authority
Validity
Not Before: Dec 9 13:27:38 2019 GMT
Not After : Apr 22 13:27:38 2021 GMT
Subject: O = Jumbo Cloud Servers, CN = jadmin
X509v3 extensions:
X509v3 Extended Key Usage:
TLS Web Client Authentication
Associate the client certificate with the Domino user
Use the following Domino server console command to load the client certificate into the Person document in the Domino directory.
This command uses the Common Name (CN) part of the name in the certificate to find the Person document and then import the certificate into it.
> load proton --importcert c:\certs\jadmin.crt
[0FE0:0002-0A5C] 12/09/2019 08:29:30.05 AM PROTON_CMD> import_certificate: c:\certs\jadmin.crt
[0FE0:0002-0A5C] 12/09/2019 08:29:30.06 AM PROTON_CMD> Certificate::init: enter
[0FE0:0002-0A5C] 12/09/2019 08:29:30.06 AM PROTON_CMD> Certificate::init: subject: CN=jadmin/O=Jumbo Cloud Servers
[0FE0:0002-0A5C] 12/09/2019 08:29:30.06 AM PROTON_CMD> Certificate::init: exit
[0FE0:0002-0A5C] 12/09/2019 08:29:30.08 AM PROTON_CMD> Updating note 0x1CF2 for 'jadmin'
Inspect the client certificate in the Domino directory
To inspect the client certificate in the Domino directory perform the following steps:
- Locate the Person document for the user in the Domino directory.
- Click on "Edit Person" button to open the document for editing.
- Click on "Examine Internet Certificate(s)" button to open the dialog box.
- Select one of the entries in the "Certificates issued by" list in the dialog to view the details of the certificate.