About Act-as-User support
The following settings control aspects of this feature for all applications using Proton. The Act-as-User feature can be used only when Client certificate authentication is enabled in Proton.
- Enable Act-as-User tokens -- To enable processing of requests with an Act-as-User token.
- Act-as-User configuration -- To allow 'Act-as-User' operations for an application, you must list the application functional ID in this configuration database for the API to allow them for.
- IAM Client Configuration Name -- To identify the credentials and the service that authenticates Act-as-User tokens.
OAuth Configuration
Proton relies on the IAM service to validate and decode the access tokens passed via the domino-db API. This operation is known as introspection and is defined by RFC 7662. The following configuration steps are necessary to allow proton to securely perform introspection calls to the IAM service:
Verify the hostname and port of the IAM introspection endpoint. This will be the value of the Issuer setting as described here
Create a resource provider on the IAM service.
- Go to the IAM Management Dashboard, click Manage
Resource Providers and create a "Resource Provider". After clicking
"Create", enter descriptive values that will identify this resource
provider as the proton resource provider. For example:
- Resource Provider Name:
Proton. - Resource Provider Description:
Proton resource provider. - Click Save. You are shown the Resource Provider ID and Resource Provider Secret. (You can come back to these if needed.)
- Resource Provider Name:
- Go to the IAM Management Dashboard, click Manage
Resource Providers and create a "Resource Provider". After clicking
"Create", enter descriptive values that will identify this resource
provider as the proton resource provider. For example:
Add the resource provider credentials to the Domino server credential store.
Linux:Open a command prompt and then run the following commands:
Note: Before Domino 11, the bin directory was in
/opt/ibm/domino/cd /local/notesdata /opt/hcl/domino/bin/tools/startup /opt/hcl/domino/notes/latest/linux/oauthcfg create proton <Resource Provider ID> <Resource Provider Secret> <https://<domino-iam-service host>/token/introspection>Windows:
Open a command prompt and then run the following commands:
cd <notes.ini-location> \<domino-program-directory>\oauthcfg create proton <Resource Provider ID> <Resource Provider Secret> <https://<domino-iam-service host>/token/introspection>See the Credential Administration page for more details.
Add a certificate capable of verifying the IAM service certificate to the proton keyring file. There are three possibilities:
- If a self-signed root CA (Certificate Authority) was used to create the IAM service certificate, then the root certificate associated with the CA needs to be added to the proton keyring.
or - If an intermediate CA was used to create the IAM service certificate (this is likely the case when using a public CA), then the certificate associated with the root CA (the certificate at the top of the certificate chain) needs to be added to the proton keyring.
or - Import the IAM service certificate into the proton keyring file.
- If a self-signed root CA (Certificate Authority) was used to create the IAM service certificate, then the root certificate associated with the CA needs to be added to the proton keyring.
Database Configuration
Applications must be given permission to perform Act-as-User operations on behalf of end users using domino-db.
Each domino-db application should use a different user in the Domino directory,
known as the application's functional id. The application's functional id must
have the _ActAsUser role in the database to be able to make Act-as-User
operations.
Furthermore, an application may or may not have access via the ACL to perform
operations with it's own identity. The minimum access that an application may
have to be able to make Act-as-User requests is Read public documents as shown
below.
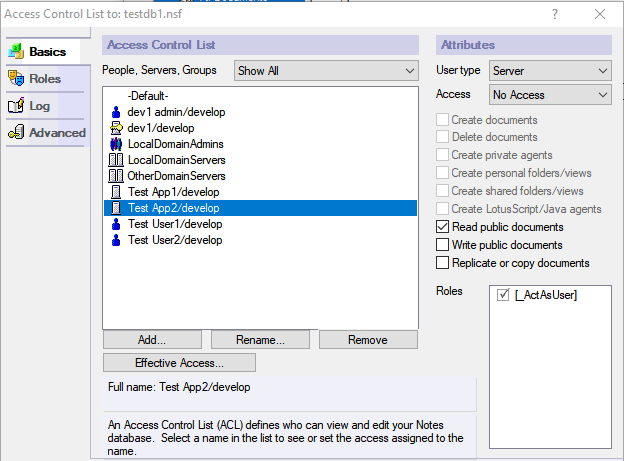
In this example, the application has Act-as-User rights, but is only able to read public documents with it's own identity.